The principles of facial recognition and the application of edge computing: the latest trends
-
-
Author: 网站编辑
-
7484
- Wx Share
-
-
Want to learn more about the application trends of facial recognition? Welcome to read the Facial Recognition Application Trend Analysis.
Time & Payroll Suite
Attendance, Payroll and Access Control Solution for Cost Reduction and Productivity Gains Details
All‑in‑one automated timekeeping and payroll system with robust, secure processes to guarantee payroll integrity. Includes leave management, shift rostering, multi‑site and chain support, multi‑ledger accounting, and comprehensive modules.
In recent years, facial recognition applications have flourished. Unlocking mobile phones using facial recognition is a prime example of its integration into daily life.

However, besides unlocking mobile phones, facial recognition is also widely used in various scenarios such as access control and security. In this article, we will delve into the principles of facial recognition, how to optimize it in various application scenarios, provide related technical details, and explore various promising applications of facial recognition.
What is Facial Recognition?
Types and Implementation Methods of Facial Recognition
Key Considerations for Building Facial Recognition on Edge Devices
Edge Device Facial Recognition: Local Devices and Workstations
Other Design Considerations: Security, Encryption Technology, and Privacy Protection
Facial Recognition Technology: Establishing Standards
Practical Applications of Facial Recognition
Future Prospects of Facial Recognition – The Most Market-Potential Artificial Intelligence Biometric Technology
1. What is Facial Recognition?
Facial recognition is a type of biometric technology. Its operating principle involves extracting facial feature values using vector methods and comparing them with the feature values of pre-registered faces. In fact, this technology has existed in the market for many years. For example, facial recognition technology has developed rapidly in the last decade, providing facial recognition functionality to identify users in front of computers and enabling quick login. Ten years ago, facial recognition mainly used digital signal processing (DSP) technology, but its inherent limitation was that it could only recognize frontal faces. In recent years, with the development of AI (Artificial Intelligence) technology, facial recognition has adopted Deep Neural Network (DNN) technology. This not only significantly improves recognition rates but also allows for the identification of faces from various angles, greatly contributing to the widespread adoption of facial recognition.
Deep Neural Network facial recognition is based on AI algorithms and complex mathematical formulas to measure various variables of the face, such as the length and width of the nose, forehead width, and eye shape, converting these variables into facial feature values. These feature values are then compared with facial feature values in a database to determine the correct identity of the face.
SEETA FACE Technology, with years of experience in AI and facial recognition technology development, has developed the SeetaFace6 AI facial recognition engine using deep learning and neural networks. Through continuous optimization and tuning, it has become one of the world's most accurate and reliable facial recognition technologies, offering flexibility for deployment on various edge devices and accelerating the application of facial recognition in the Internet of Things (IoT).
1.1 Main Functions of Facial Recognition
Facial recognition is currently recognized as the most accurate and widely usable artificial intelligence biometric technology. Besides common facial detection and identity verification, facial recognition technology also includes feature detection (such as gender, age, and emotion), mask detection, and other functions. Furthermore, facial recognition technology can reduce the bias caused by human judgment.
Taking SEETA FACE 6 as an example, the main functions of facial recognition include:
Face Detection
Face detection is the first step in facial recognition. Through face detection technology, even if only a portion of a face appears in the image, its location can still be accurately scanned, detected, and bounded within the video or image. In face detection, fast and real-time face detection is the most important indicator of recognition performance and is the foundation of facial recognition. For example, SEETA FACE 6 can detect multiple faces in the same frame and accurately track and bound them one by one.
Facial Feature Extraction
Facial feature extraction is the next step in facial detection. The facial recognition engine can segment the bounding box of a face into n dimensions. For example, a high-precision facial recognition engine with n=1024 can segment the face into a 1024-dimensional matrix, extracting vector-based facial feature values. These extracted feature values can then be compared with the most similar data in the database to determine the correct identity.
Facial Recognition
The facial feature values extracted by the facial recognition engine can be compared with the feature values of pre-registered faces in the database to identify the correct identity. For example, a 1:N comparison compares the feature values of the face appearing in the image with N pre-registered faces in the database to identify the identity. Using SEETA FACE 6 as an example, the extracted feature values are encrypted and cannot be used to deduce the face. Furthermore, no facial images are stored during the recognition process, effectively ensuring personal data security.
1.2 More Face-Related Functions
Besides the basic face recognition mentioned above, more applications related to face recognition are as follows:

Facial Feature Detection
Facial feature detection can be used to analyze information including gender, age, emotion, and head movements (such as nodding, shaking, etc.). It is mainly applied in smart retail scenarios, such as electronic signage, for targeted advertising or analyzing visitor statistics.
Using face recognition to detect visitor age, gender, emotion, and other information
Mask Detection
During the pandemic, mask detection was one of the most popular applications, used to ensure that visitors in public or private places are wearing masks correctly and to perform identity verification when wearing masks, thus protecting health and visitor safety. SEETA FACE 6 can detect whether visitors are wearing masks or improperly wearing masks (e.g., mouth and nose exposed, or hands covering mouth and nose), and can perform highly accurate identity recognition even when masks are worn.
Using facial recognition technology to detect correct mask wearing
Identity recognition (supports mask wearing) Mask wearing status Body temperature measurement information

Liveness detection and anti-counterfeiting
Common methods of cracking facial recognition include using photos or videos of faces for hacking and identity theft. Therefore, liveness detection is crucial for facial recognition applications. Common liveness detection methods can be performed using 3D or 2D cameras.
When using a 2D camera (e.g., a webcam or a regular mobile phone front camera), liveness detection can be performed through interactive or non-interactive methods. Interactive methods utilize head commands (e.g., nodding, shaking) or facial expressions (e.g., blinking, opening mouth) for liveness detection. Non-interactive methods rely on proprietary algorithms developed by each developer for authenticity verification.
When using a 3D depth camera, liveness detection is primarily achieved through depth information. No additional interactive methods are needed when using 3D depth information. 3D depth cameras typically offer more immediate and intuitive liveness detection than 2D liveness detection; however, they require specialized hardware and are more expensive to implement. In contrast, 2D liveness detection is compatible with existing device cameras and provides a certain level of accuracy. SETA FACE supports liveness detection using both 2D and 3D depth cameras. SEETA FACE 6 supports 3D depth cameras including Intel RealSense™, 3D structured light cameras on iPads and iPhones, etc.
The most prestigious global competition for liveness detection is currently the IEEE ICCV Anti-spoofing Challenge. ICCV, a biennial research conference held by the IEEE (Institute of Electrical and Electronic Engineers), is one of the top conferences in the field of computer vision and a benchmark event for academia, industry, and researchers.
The Anti-spoofing Challenge, held at ICCV 2021, was open to companies, research institutions, and academic groups worldwide. This competition uses highly realistic 3D masks as the competition item, unlike previous tests that used 2D photos or videos. The emergence of highly realistic 3D masks poses a significant challenge to many current facial recognition technologies.
In the 2021 competition, a total of 195 teams from around the world participated, with 56 teams advancing to the final stage. Only 18 teams achieved the required standard, ranking among the leading teams in the ICCV liveness detection competition. In the final results, the SEETA FACE 6 SDK achieved a 96.8% anti-spoofing rate (average error rate of 3.215), ranking third globally in liveness detection technology and leading the top-ranked algorithm excluding Chinese and Russian teams. Furthermore, SEETA FACE 6 was only 0.16% behind the top-ranked algorithm.

Used in ATMs to detect whether the person is real or using a photograph to steal identity.
1.3 Accuracy of Face Recognition
The accuracy of face recognition can be judged by a low non-match rate (FNMR) and an extremely low false match rate (FMR). False Match Rate (FMR) indicates that a person is mistaken for another person, while FNMR indicates that two photos of the same person cannot be matched.
The Facial Recognition Vendor Test (FRVT) conducted by the National Institute of Standards and Technology (NIST) uses a set of standardized metrics to evaluate the accuracy of various facial recognition algorithms. NIST FRVT uses four test items for comparison, comparing real photos with photos from the following four test sets:
VISA Photo Comparison: ID photos (such as passports, visas, ID cards, driver's licenses, etc.) must be clear, front-facing, and unobstructed.
VISA Border Photo: Photos taken during border checks using standard cameras (such as webcams). These are more prone to overexposure or poor lighting, but the shooting angle is generally more controlled than a wildcard photo, and is closer to a frontal angle.
Police File Photo Comparison Search (Mugshot): Police-filed photos of criminal suspects, while similar to VISA photos (front-facing), may show a wider age range, often exceeding 12 years.
Wild Photo Comparison Search: Photos taken in unrestricted environments (e.g., via IP camera), often with variations in lighting, angles, partial obstruction, low light, high noise, or poor image quality.
The SEETA FACE 6 performed exceptionally well in the NIST FRVT VISA test, achieving a 99.7% recognition rate with a false positive rate of 0.3% FNMR/1/10,000 FMR. Furthermore, it achieved a 99.06% recognition rate (1/1 million false positive rate) in the VISA Border test and a 96.88% recognition rate (1/100,000 false positive rate) in the WILD test. Taking Face ID, commonly used in smartphones, as an example, it offers a 96% recognition rate (with a false recognition rate of 1 in 10,000), indicating that SEETA FACE 6 provides relatively accurate and reliable facial recognition.
Besides the algorithm, another factor affecting facial recognition accuracy is the camera's image quality, such as resolution, angle, lighting, lens sharpness, and camera type. Facial recognition engines generally use footage captured by a 720p camera, but 1080p resolution is recommended for higher recognition accuracy. The camera should be positioned directly facing the subject, in good lighting, and with a clean lens.
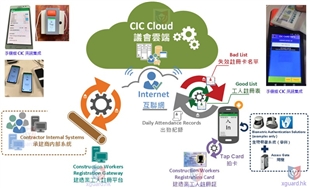
Facial recognition technology deployment types mainly include "cloud-based facial recognition services" (such as Microsoft and AWS) and "edge device facial recognition." Both types have their advantages. Generally, edge device facial recognition is built on edge devices through SDKs or software, offering faster recognition speeds, security, flexibility, and cost-effective deployment. 2.1 Cloud-based Facial Recognition Services
When using cloud-based facial recognition services, a stable and uninterrupted network connection is essential to stream video footage captured by the camera to the cloud for facial detection and feature extraction. Because the captured images are transmitted over the network and stored on servers, in addition to unavoidable latency, bandwidth costs are high, and cloud services pose certain risks, including potential leakage of facial images and security vulnerabilities that could lead to hacking.
However, cloud-based facial recognition services also have their advantages. Since facial recognition processing is performed on cloud servers, unlike edge-based camera devices, hardware with AI computing capabilities is not required. Before the advent of various AI-enabled chips, early facial recognition technologies primarily relied on cloud-based technologies. Representative vendors of cloud-based facial recognition include:
Microsoft Azure's Face API
Google's Vision AI
AWS's Rekognition
For small-scale deployments, such as security systems for homes and small offices, and smart doorbells, cloud-based facial recognition services are suitable for developers where bandwidth costs are not high.
2.2 Edge Device Facial Recognition
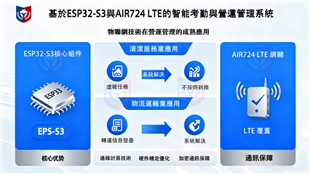
In recent years, the application of facial recognition technology in various edge devices has been increasing, such as smart locks, mobile devices, point-of-sales (POS) systems, interactive information kiosks, and electronic billboards. When facial recognition runs on edge devices, it can provide real-time facial detection and recognition because there is no need to wait for facial images to be uploaded to the cloud, resulting in excellent recognition rates.In most edge-device facial recognition applications, face detection and feature value extraction occur at the edge. When comparing data against a database, regardless of whether the facial data is stored on the edge device or in a cloud database, the comparison is based on extracted feature values (for example, in SEETA FACE 6, the feature value file size is only 3KB). Therefore, the time for data upload, comparison, and feedback is significantly shorter than cloud-based facial recognition, typically completed within microseconds.
In recent years, the computing power of AI edge devices has increased dramatically, enabling facial recognition applications in various scenarios. For example, many financial institutions lack internet connectivity for security reasons; therefore, implementing facial recognition in these settings necessitates heavy reliance on edge computing devices.
Face recognition on edge computing devices offers low deployment costs and high scalability, making it the preferred choice for various facial recognition applications.

SEETA FACE 6 AI Face Recognition SDK runs on Windows, Linux, Android, and iOS operating systems.
The SEETA FACE 6 AI face recognition engine is a face recognition SDK (Software Development Kit) specifically developed for edge devices. It can be flexibly integrated into various edge computing devices and widely supports various chips and operating systems. It has achieved outstanding performance in the globally renowned NIST FRVT face recognition technology benchmark test. SEETA FACE 6 can be flexibly deployed in various IoT application scenarios, such as security, access control, public safety, smart finance, smart retail, smart cities, and smart homes, providing a secure, reliable, and high-recognition-rate face recognition solution.
2.3 Facial Recognition Applications on Edge Devices: A Major Future Trend
Next, let's further explain this from three aspects: (1) deployment cost, (2) response time, and (3) service availability.
2.3.1 Deployment Cost
AI (Artificial Intelligence) heavily relies on computing power. Cloud-based facial recognition is typically priced based on the number of faces processed. For small-scale deployments, such as home smart locks processing only a few facial images per hour, cloud-based facial recognition can be considered. However, for larger deployments, such as security systems or office access control systems that need to recognize hundreds or thousands of faces per hour, edge computing is a better choice. It's worth noting that with more and more chips supporting AI computing and significantly reduced hardware costs, deploying AI facial recognition on edge devices is a better long-term option.
2.3.2 Response Time
On edge devices, top-tier algorithms can complete facial recognition computations within milliseconds. In contrast, cloud-based facial recognition requires waiting for real-time image streaming to the cloud and processing, often taking several seconds. For many practical applications of facial recognition, processing time is crucial. For example, access control systems typically need to complete identification and unlocking within microseconds to be usable. Other applications such as security control, facial recognition transactions and payments, and identity verification also have extremely high requirements for facial recognition response time. In these cases, edge device facial recognition, with its short response time, has a significant advantage.
2.3.3 Service Availability
A network connection is essential for using cloud-based facial recognition. However, in many application scenarios, if the network connection is unstable or even unavailable, cloud-based facial recognition will be unusable. Imagine if your smart lock relies on a network connection for facial unlocking, but unfortunately the network connection drops—what would happen?
In comparison, building facial recognition on edge computing devices is a better choice, as it can operate normally even without a network or in environments where a network cannot be established. Next, we will explore the advantages of building facial recognition on edge devices in more detail.
3. Key Considerations for Building Facial Recognition on Edge Devices
When building facial recognition edge devices, selecting the appropriate chip based on different application scenarios and contexts is crucial, as the choice will affect cost and performance. For example, high-end NVIDIA GPU chips are relatively expensive, but their computing power can handle video feeds from hundreds of cameras simultaneously in security scenarios, reducing the number of workstations needed in large-scale security applications and significantly lowering costs. On the other hand, low-cost SoC chips from MediaTek, Qualcomm, or NXP, while having relatively lower computing performance (approximately 5 frames per second, only sufficient for frontal facial recognition), possess low power consumption and low heat generation characteristics, meeting the needs of most AIoT applications and being more suitable for lightweight devices.
3.1 Dedicated Chips or System-on-a-Chip (SoC)
AI chips or System-on-a-Chip (SoC) are crucial factors influencing facial recognition optimization. Chip manufacturers such as Intel, NVIDIA, MediaTek, NXP, and Qualcomm offer comprehensive solutions, providing corresponding advantages for different usage environments. Each chip integrates an AI inference engine and is designed with varying computing power, device size and form factor, and power consumption in mind.
Chip giants like NVIDIA, Intel, Qualcomm, MediaTek, and NXP have seized the initiative in edge and IoT AI technologies, rapidly introducing new APUs (AI Processing Units), VPUs (Vision Processing Units), and NPUs (Neural Network Processing Units) to the market, accelerating image processing and AI inference while simultaneously optimizing performance and reducing power consumption.
The next section provides a comparison of most SoCs, GPUs, and VPUs on the market that support facial recognition engines (such as FaceMe®).
3.1.1 Dedicated GPU or VPU
These dedicated chips utilize a dedicated Graphics Processing Unit (GPU) or Visual Processing Unit (VPU) for computation, providing dedicated, high-performance AI computing, such as AI facial recognition. When building such systems, a Central Processing Unit (CPU) is required.
3.1.2 GPU/NPU/APU Integration in CPU/SoC
Integrating the CPU and a dedicated GPU/NPU/APU for AI computing into the SoC provides a simpler and more cost-effective solution, easily enabling the adoption of facial recognition technology even in lightweight IoT devices.

3.2 Operating System
Various chips have their own supported operating systems (OS). A good facial recognition engine should support a variety of chip and operating system combinations. Taking FaceMe as an example, it is compatible with the vast majority of chips and operating systems on the market, and supports more than 10 operating system and chip combinations:
Windows
Android
iOS
Various Linux distributions
Ubuntu x64,
Ubuntu ARM,
Red Hat,
JetPack (mainly for NVIDIA Jetson family),
CentOS,
Yocto ARM
SEETA FACE 6 can be applied to multiple fields, providing flexible and customized solutions for different hardware configurations (such as the chip and operating system) to meet the application needs of various scenarios. Supporting various operating systems, it is suitable for multiple cross-platform solutions. Developers can choose to enable GPU/VPU acceleration on hardware such as NVIDIA CUDA™ and Intel Movidius™, or enable performance optimization for IoT/AIoT devices using NVIDIA Jetson™ and ARM. Furthermore, it supports various AI logic inference engines such as OpenVINO™, TensorRT, Qualcomm SNPE, and MediaTek NeuroPilot. Therefore, it can be quickly implemented regardless of hardware configuration or architecture, accelerating the computation speed of deep learning algorithms.
3.3 Achieving Optimal Performance Through System Architecture Optimization
Executing facial recognition technology on high-performance workstations or PCs with built-in GPUs (or VPUs) is no easy task. Dozens of image streams continuously flow between the CPU, GPU, and memory in the system bus. Without optimization at the system architecture level, even top-tier facial recognition algorithms cannot achieve fast and accurate recognition rates. Therefore, the system architecture design should reduce the amount of data transfer between the CPU, GPU, and memory.
Through continuous optimization of the system architecture, SEETA FACE 6 delivers excellent recognition performance. For example, on a single workstation, the SEETA FACE 6 paired with an NVIDIA RTX A6000 chip can achieve a processing speed of 256-416 frames per second (actual data will vary depending on the specific SEETA FACE 6 face recognition model). This is equivalent to each workstation simultaneously processing 25-41 video streams (assuming a recognition frequency of 10 frames per second per stream), providing the market with an excellent cost-performance face recognition solution.

3.4 Lightweight AI Face Recognition Model
Face recognition has a wide range of applications. For example, in applications that only require a frontal view, such as smart door locks, a lighter face recognition model can be used to implement face recognition on lower-cost devices. SEETA FACE 6 offers three models to meet various application needs:
• Ultra High Precision (UH): This solution provides excellent and accurate recognition rates for both frontal ID photos and wide-angle real-world photos. Therefore, it requires a high-performance computing device, such as a GPU, VPU, or a high-end Intel CPU.
• Very High Precision (VH): This solution also performs face recognition for frontal photos and wide-angle real-world photos. Its accuracy is only slightly lower than the SEETA FACE 6 Ultra High Precision model, but it doesn't require the high-end computing power of the Ultra High Precision model, thus balancing high accuracy with affordability.
• High Precision (H): This solution is suitable for low-cost chips with lower computing power. It provides high accuracy for photos that only require recognition of relatively frontal faces.
4. Edge Device Facial Recognition: Local Devices and Workstations
SEETA FACE 6 is a world-leading AI facial recognition engine, compatible with various hardware devices for flexible deployment. SEETA FACE 6 can be easily deployed in various workstations, computers, mobile devices, and IoT devices. Related case studies are as follows:
Facial Recognition Applications in Workstations
In security applications, a single workstation can handle dozens or hundreds of IP camera video streams simultaneously by installing one or more GPU cards. In large venues such as department stores, airports, factories, or hospitals, it is often necessary to handle video streams from dozens or even hundreds of cameras for personnel access control, visitor behavior analysis, crowd management, and VIP customer identification. Connecting one or several workstations to all cameras in the venue for facial recognition technology provides the simplest, most reliable, and cost-effective solution.
For more information on the applications and advantages of SEETA FACE 6 in workstations, please refer to their facial recognition security solution.
Facial Recognition Applications on Personal Computers
In small-scale applications, such as shops or restaurants, personal computers can be used for facial recognition applications, such as VIP identification, employee attendance management, and blacklist alerts. In the era of the pandemic, ensuring that all personnel entering and exiting buildings are wearing masks and have normal body temperatures has become a daily necessity. Therefore, shop or restaurant managers can install IP cameras or USB cameras at the front and back doors and connect them to PCs with facial recognition software installed for personnel health and security management. CyberLink's affordable, ready-to-use FaceMe Security solution meets the needs of the pandemic era.

Applications of Facial Recognition on Mobile Devices
Facial recognition technology on mobile devices is no longer limited to unlocking phones. In the field of smart fintech, facial recognition technology for electronic Know Your Customer (eKYC) on mobile phones can enhance the accuracy of identity verification in online banking, loan applications, and insurance applications.

Applications of Facial Recognition on Smart IoT Devices
Edge computing innovations not only improve device performance but also reduce deployment costs, enabling the widespread application of facial recognition on IoT devices. Smart Kiocks are a prime example. For frequent travelers, the technology used in global entry and airport fast-track security checks via facial recognition is certainly familiar. Currently, smart self-service kiosks equipped with facial recognition technology are also widely available.Widely used in fast-food restaurants, medical institutions, and hotels. Furthermore, self-service check-in systems have been implemented in large hotel chains to save queuing time. Adopting facial recognition technology (such as FaceMe®) can provide consumers with an excellent user experience, allowing them to use their faces throughout their journey instead of traditional identity verification methods.

5. Other Design Considerations: Security, Encryption Technology, and Privacy Protection
As mentioned earlier, cloud architecture requires capturing personal photos or videos and connecting them to cloud servers for processing, a process undoubtedly vulnerable to attack and leakage. Compared to cloud architecture, edge architecture facial recognition is far more secure. When deployed at the edge, all data is stored only in the form of encrypted facial feature values, and the entire process does not require connection to the cloud, significantly reducing risk. All SEETA FACE 6 data is secure before being stored in any database using AES-256-bit encryption. AES is one of the best symmetric encryption algorithms, and 256 bits represents the highest level of security. Because facial feature data is encrypted with a key and stored separately from the original data and platform servers, it is fully protected and cannot be read even if the hardware is damaged or stolen.
Please note that each person must select a designated facial recognition program to bind their facial photograph. In edge architecture solutions, the captured information includes facial feature data (captured through high-dimensional extraction) for future comparison and identification. This feature does not contain an actual face image, cannot reconstruct a face, and is stored separately from all personally identifiable information.
The encrypted data obtained for facial recognition can only be used to match registered feature values stored in a secure database. Many data privacy laws and regulations (such as GDPR, CCPA, BIPA, and LGPD) treat biometric data as personal information; therefore, any company needing to implement facial recognition must obtain user consent before binding faces.
When evaluating facial recognition providers, special attention must be paid to the location of their headquarters and critical equipment. The US government has expressed considerable concern about surveillance technologies from companies headquartered in China and Russia, as they may lack sufficient providers or even a need to protect personal data. Most facial recognition solutions are secure and adhere to fairly stringent data and privacy protection standards. However, as an end-user, your service provider should inspire your complete trust, especially regarding security, privacy, and human rights protection.
6. Facial Recognition Technology: Setting Standards
As facial recognition and biometric technologies develop and expand, they are likely to fundamentally change various aspects of our lives. While facial recognition technology has enormous potential to improve public safety, security, and customer experience, we cannot ignore the potential risks it poses. Recent public safety incidents involving facial recognition technology have prompted advocacy groups to rethink facial recognition and criticize its potential biases and privacy violations.
In the United States, while there are currently no federal regulations governing facial recognition, some states have drafted regulations and procedures. Illinois was the first state to address facial recognition, passing the Biometric Information Privacy Act (BIPA) in 2008, which provides strict regulations on how private companies collect and use biometric data (including facial data). Approximately ten years later, in 2020, the California Consumer Privacy Act (CCPA) came into effect, giving residents the right to demand that companies disclose how and what data (including biometric data) they collect, and reserving the right to require the deletion of that data. Washington state also passed a law, effective in 2021, requiring all government agencies (such as law enforcement) to use the technology with complete transparency.
Furthermore, despite discussions regarding federal regulations, including the proposed Facial Recognition and Biometric Technology Moratorium Act in June 2020, it has yet to take effect.
In light of this, CyberLink adheres to ethical standards; however, we believe facial recognition technology should not be completely shut out. We strongly encourage legislators to develop regulations protecting individuals, while hoping this technology can comprehensively enhance societal security and convenience. Pioneers in this field must lead by example, openly sharing how the technology operates, how it is applied, and how personal privacy is protected.
7. Practical Applications of Facial Recognition
Today, facial recognition, due to its security, ease of use, and enhanced user experience, has been implemented in many industries and scenarios – even though many usage guidelines remain to be defined. A recent survey by the Security Industry Association (SIA) found that a majority of Americans (68%) believe facial recognition can make society safer, with the technology particularly supported in airports (75% adoption rate among airlines; 69% adoption rate among the Transportation Security Administration), office buildings (70%), and the banking industry (68%). While we cited many case studies in the preceding overview, the following sections will introduce more application examples and highlight the key aspects of each.
The main success stories can be categorized into five main areas:
Access control, such as: personnel access management, smart medical cabinets, smart door locks
Surveillance security systems, such as: detecting unauthorized personnel in warehouse areas
Identity verification, such as: using eKYC (electronic Know Your Customer), a major application of BFSI (banking, financial services, and insurance)
Smart retail, such as: collecting statistics on in-store customers
Health management during the pandemic, such as: detecting whether masks are worn correctly
SEETA FACE 6 Security provides a comprehensive range of facial recognition applications for surveillance security systems.

SEETA FACE 6 can be easily deployed on a PC, connecting to a thermal imaging camera via USB to perform contactless health measurements, ensuring safety in offices, stores, or restaurants.
AI biometric technology is also driving applications in specific vertical sectors, such as:
Manufacturing and Warehouse Management
Industrial equipment, production lines, and warehouses typically require strict access control for employees and visitors, as well as identity verification for employees operating machines and equipment. Facial recognition provides a comprehensive solution. Furthermore, during the pandemic, facial recognition can ensure warehouse personnel wear masks properly in accordance with new social distancing regulations.
Using Facial Recognition Technology for Hospital Personnel Management
Public Transportation and Airport Management
Facial recognition applications are increasingly appearing in airports and train stations, from interactive kiosks (e.g., fast-track immigration systems and global entry programs) to automated boarding systems and security monitoring. The COVID-19 pandemic has exacerbated the challenges of maintaining a safe and healthy environment in transportation hubs with high passenger volumes. Facial recognition can help address these challenges by enabling contactless boarding and health checks, monitoring whether passengers are wearing masks correctly, and ensuring that only passengers without fever can board planes, trains, and buses, reducing the risk of infecting others.

Using facial recognition technology in airports
Smart offices, smart homes, mixed-use residential complexes, medical institutions, and tertiary institutions
Smart city innovations (including smart offices, smart homes, and mixed-use buildings) are rapidly developing, and the demand for access control, security, and health monitoring systems is also increasing significantly, including in schools and hospitals. Maintaining security manually is often very expensive. Facial recognition can automate many access control and monitoring tasks, making them safer.
Using Facial Recognition for Smart Office Access Control
Smart Retail
Facial Recognition Technology

Innovating the retail market and providing a new and engaging customer experience, this technology not only provides accurate foot traffic statistics but also enables targeted advertising on digital billboards, VIP customer identification, and the collection of data such as visitor age, gender combination, emotional state, and time spent in specific areas.
Targeted advertising based on age and gender on digital billboards
Smart Finance and Banking
eKYC (electronic Know Your Customer) is a popular technology in the financial industry in recent years, strengthening identity verification and preventing fraud. Facial recognition provides a perfect solution for eKYC in online and physical banks, including user identity verification at ATMs and identity verification for loan or insurance applicants to protect the security of online transactions. Facial recognition can also warn security personnel before blacklisted individuals enter the bank or commit a crime, significantly enhancing the security of banking institutions.
Facial verification at ATMs
Smart Catering and Hotel Management: Restaurants, Bars, Hotels
For hotel operators, facial recognition offers significant advantages, providing an instant personalized experience. When a VIP enters the hotel, the reception staff will be automatically notified. Furthermore, facial recognition can control customer access to specific areas, allowing customers to select the correct elevator and floor and unlock designated room doors.

Fast food restaurants have also invested heavily in self-service ordering machines, digital electronic signage, curbside pickup machines, and drive-thru services. Points-based reward programs are fully integrated into these systems, typically involving a password and a few steps via a mobile app. If fast food operators were to implement facial recognition, it could effectively simplify the previously cumbersome points-based reward process, enhance the interactive experience, and thus improve the service quality of fast food restaurants.
Self-service ordering machines using AI facial recognition

Future Prospects of Facial Recognition – The Most Promising Artificial Intelligence Biometric Technology
The emergence of facial recognition technology will make our world a better place, but to achieve this, broader and more rigorous ethical standards are needed for its commercial and public sector applications, allowing individuals worldwide to dispel doubts and accept this emerging artificial intelligence biometric technology as a new security standard.
Facial recognition has immense potential. Businesses can use it for workplace security to protect employee safety; retailers can use it in stores to enhance customer experience; manufacturers can use it to strengthen personnel control in restricted areas; and the fintech industry can use it to introduce more robust and secure authentication mechanisms. In the foreseeable future, facial recognition holds immense potential in many application areas.
Facial recognition represents the future of artificial intelligence biometrics. However, manufacturers must use this technology cautiously and address concerns through appropriate regulations and user education. The goal is to allow consumers to experience and accept the advantages of facial recognition without hindering innovation, ultimately leading to its adoption.
Software Service
Industry information
- Views 8944
- Author :Tony
- Views 603
- Author :Tony
- Views 1661
- Author :Bruce Lee
- Views 41
- Author :Tony
- Views 15
- Author :Bruce Lee
- Views 29
- Author :Tony
































































Hardware & Software Support
We are deeply rooted in Hong Kong’s local services, specializing in hardware and software issues.
System Integration
Hardware and software system integration to enhance stability and reliability.
Technical Support
Professional technical team providing support.
Professional Technical Services
Focused on solving problems with cutting‑edge technologies.